The Network Remembers Everything
August 15-17, 2025
"Trust us, we're professionals" 😏
* Statistics and accuracy of data may be questionable given AI may or may not have been involved in the production of this presentation
The Network Remembers Everything
August 15-17, 2025
"Trust us, we're professionals" 😏
* Statistics and accuracy of data may be questionable given AI may or may not have been involved in the production of this presentation
Providing open, fast, and watched network connectivity
FortiGate in Monitor Mode =
WE SEE YOUR SINS BUT LET THEM HAPPEN
"Your packets are our entertainment" 🍿
Total Data Transferred (Final Count)
604 GB Internal + 1.94 TB External
Top Traffic Destinations:
Google: 292 GB | Fastly: 159 GB | Apple: 131 GB
Tzulo: 117 GB | Amazon: 114 GB | Cloudflare: 93 GB
3.7 BILLION packets processed 🤯
Data per device: 1.6 GB @ HOPE vs 1.2 GB @ DEFCON
8x fewer devices, 1 less day, but MORE consumption per device and 10x the available bandwidth 💪
+ many volunteers crimping cables, only 2 gave up
Hiding in Tobin 211 (We had FBI sandwiches, donuts, shot glasses & swag waiting for you!)
Fun fact: 14 people tried to ARP poison us. Nice try!
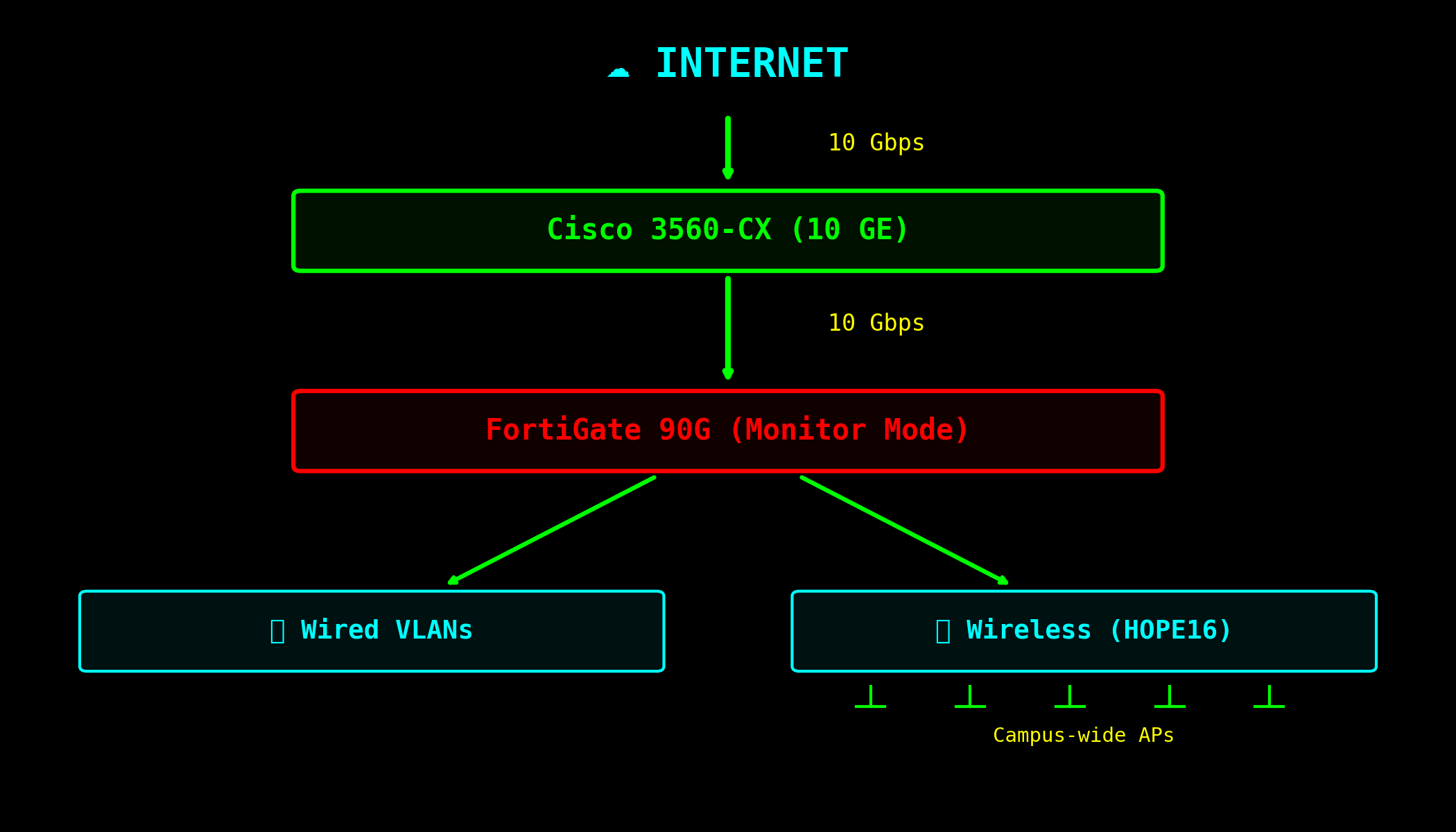
10 Gbps of pure, unfiltered connectivity

Plus painters tape across the ENTIRE campus. No, we're not apologizing.
Don't worry, we're crimping better cables for next year.
🎯 The Technical Flex:
FortiGate → webhook.php → parse data → update JSON → AJAX polls → live charts
Built in 3 hours with Claude AI because who needs sleep? ☕
Hourly updates for 3 days straight | People actually F5'd for traffic stats!
⚠️ Y'all Need Something (and a Firewall) ⚠️
Check your systems. Seriously. You're owned.
🎭 Peak hostname creativity - You magnificent weirdos!
We built a fancy dashboard...
Only 43 people visited
Meanwhile, 1,374 tried to hack it 🤦
Pro tip: It's literally just PHP. Save your 0days.
Viruses Downloaded: 0 (but we're not decrypting TLS, so... 🤷)
172.31.3.218 wins the "Most Infected" award with 6 PUAs! 🏆
Smart hackers using VPNs to hide from us:
ProtonVPN (4%), SurfShark (3%), NordVPN (2%), IVPN (1%)
Others using WireGuard, OpenVPN, DoH: 10%
We respect the paranoia. This is the way.
Someone's definitely on a list now...
NSA has entered the chat 👀
308 GB to sketchy providers!
If you connected to these, your box is probably a bot now 🤖
Top Offenders:
🥇 172.31.2.141 - WireGuard psycho (133K packets)
🥈 172.31.1.190 - NFS abuser
🥉 172.31.4.160 - ICMP scanner
10.36 GB of Kerberos traffic? 10.07 GB of ICMP? Y'all wild.
🤔 UNVERIFIED REPORT
"Someone said we attacked DNS servers"
Our response: "PCAPs or it didn't happen"
Investigation Result:
No evidence found. Probably a false flag. 🙄
We monitored everything. If we did it, we'd know.
"But seriously, stop attacking DNS servers, whoever you are."
104 Countries Connected
200+ Unique ASNs Reached
From NYC Mesh to Netherlands
Remember: TLS is not optional, it's 2025 FFS
*Perfectly balanced, as all things should be
🔥 Hackers: Passionate about security AND insecurity 🔥
172.31.1.149: 103 GB?! Were you torrenting the entire Library of Congress? 📚
"Have you tried turning it off and on again?" - The UPS did that for us
🔒 The NOC Was Protected By:
⚠️ Multiple after-hours "visitors" detected
Nice try, but we saw you 📸
(Evidence attached →)

Exhibit A: "Just checking if it's open"
🎢 Classic conference pattern: Dead → Chaos → Party → Hangover → Ghost town
🎓 ST. JOHN'S UNIVERSITY 🎓
IT Team & Public Safety
You are the REAL MVPs! Without you, none of this would be possible.
Fortinet
Axcelx
St. John's IT: For the bandwidth, patience, and blind trust
St. John's Public Safety: For protecting us from ourselves
Your support made this chaos possible! ❤️
Seriously though, CHECK YOUR SYSTEMS
grep -r "Tsyndicate" ~/
Come help us tear down at Tobin 211 after this!
(We still have donuts, shot glasses, and swag!)
Stay paranoid, friends! 👾
- NOC Team: Alex, James & Jesse
P.S. - Change your passwords. All of them. Now.
ALL YOUR NETWORKS ARE BELONG TO US
🔒 YOUR DATA HAS BEEN ENCRYPTED 🔒
2.54 TB EXFILTRATED | 1,699 DEVICES PWNED | 847 VULNERABILITIES EXPLOITED
⚠️ DO NOT ATTEMPT TO RECOVER ⚠️
DO NOT SHUT DOWN YOUR COMPUTER
DO NOT CALL LAW ENFORCEMENT
DO NOT TRY TO DECRYPT FILES
TO DECRYPT YOUR NETWORK:
1. IMPLEMENT IPv6 WITHIN 24 HOURS
2. REMOVE ALL WINDOWS XP MACHINES
3. STOP USING TELNET IMMEDIATELY
4. RUN: grep -r "Tsyndicate" / --now
TIME REMAINING: 23:59:59
HOPE XVI NOC :: TERMINATED